Slideshow
-

Cute Kajal Agarwal
Telugu Movie WP -

The hottest lips are seeing red
Actress WP -

17 Cheating Pictures Collection
Adults Only -

10 Unique Houses From Around the World
Scenery Wallpapers -

Small Birds have big Love
Birds WallPapers -

Cute Kiss
Love Wallpapers -

Black Taj Mahal
Truth About Blak Taj Mahaal -

India Festival Art painting
Oil Pinting Wp -

beautiful sceneries wallpapers
Scenery WP -

Cat And Bird Cute Friendship
Birds WP -

ed ed 6 Most Popular Ways Of Couple Hugging
Adults WP -

Indian Village Paintings
Oil Pinting Wp -

Awsome moments on well & girls
Oil Painting Wp -
hansika visits simbu birthday party
Actress WP
Google crawl date using PHP source code. Google bot crawls every web site after a specific period. You can check that date using Google’s cache command in Google search engine. Here it is the example of Google cache.
http://64.233.183.104/search?q=cache%3Afree-computer-tips.info&sourceid=navclient-ff&ie=UTF-8&rlz=1B3GGGL_enPK238__238
I created PHP function which gets Google bot crawl date and returns in a form of string.
You can use these codes in your PHP applications.
Code are under the marks due to setting of page
function google_crawl_date($url){
$output = file_get_contents('http://64.233.183.104/search?q=cache:'.
urlencode($url).'&sourceid=navclient-ff&ie=UTF-8&rlz=1B3GGGL_enPK238__238');
$match_expression = '/appeared on (.*). The
preg_match($match_expression,$output,$matches);
if ($matches[1]=="") return "No Date found";
else return $matches[1];
}Usage of function above
PHP programmers need sometimes current page URL to show or save in database. There is no built-in function exist in PHP to get current page url. I made a function to show current page URL.
I used the following built-in $_SERVER array in this function. If you want to show all element return by $_SERVER array then you can use these commands.
.
.
.
.
echo "All elements by $_SERVER will appear in your browser window."; print_r ($_SERVER); echo "";
I made function which returns current page URL:
Example using function above:
echo currenturl(); ?>
?>
How to get visitors IP address? If you want to get your web site visitor’s IP address then PHP provides you complete solution for this. I made a function to get IP address of visitor.
PHP Codes
.
.
.
.
.
.
function visitorip() {
if (getenv(‘HTTP_CLIENT_IP’)) $ip = getenv(‘HTTP_CLIENT_IP’);
elseif (getenv(‘HTTP_X_FORWARDED_FOR’)) $ip = getenv(‘HTTP_X_FORWARDED_FOR’);
elseif (getenv(‘HTTP_X_FORWARDED’)) $ip = getenv(‘HTTP_X_FORWARDED’);
elseif (getenv(‘HTTP_FORWARDED_FOR’)) $ip = getenv(‘HTTP_FORWARDED_FOR’);
elseif (getenv(‘HTTP_FORWARDED’)) $ip = getenv(‘HTTP_FORWARDED’);
else $ip = $_SERVER['REMOTE_ADDR'];
return $ip;
}
echo “Your IP address is “.visitorip();
?>
In result web site visitor’s ip address will appear. In example above i made a function named visitorip() will check all conditions for getting ip and will return ip address. echo command of PHP will receive ip address will display on page.
Configuring your Gmail account in Microsoft Outlook would become as easy as 1, 2, 3 for you after reading the below mentioned step by step process. Gmail messages can now be retrieved with the help of any device or client which can provide POP support and Microsoft Outlook is one of those clients that offer POP support to their users. Just concentrate and read the every step carefully to understand the whole process:
POP Option Enabling in Gmail:
- First of all login to your Gmail account Then click on “Settings” option which can be seen on right top of your screen
- There you will find “Forwarding and POP / IMAP” option, click on it
- There an option i.e. “Enable POP for All Mails” or “Enable POP for Mail” should be clicked
- Now an action would be asked to choose after getting POP access from Gmail. Choose appropriate one that suits your need
- Check “Configure your POP client” and then a button saying “Save Changes” should be pressed
- We consider that you have already opened Microsoft Outlook 2007, click Tools Menu
- Click an option “E-mail Account”
- There you will see an option “Add a new e-mail account” select it and then click on the button “New”
- There you will be asked by the system to select server type. POP3 or POP option must be selected ….. then click on the option “Next”
- Now system will ask for necessary setting. Put on your desired / required setting including email address and password of your email
- Write “pop.gmail.com” as your incoming mail server and as the settings of outgoing mail server “smtp.gmail.com” must be written in the required field
- Then click on the button that says “More Settings . . .”
- Then click on the tab saying “Outgoing Server” and an option saying “My outgoing server (SMTP) requires authentication” must be checked by you. It will increase security and a password will be required to even send a single email from this Microsoft Outlook in addition to receiving email
- Then on the same screen, you will see a tab saying “Advanced”, click on it
- Here you will have to change port numbers for your incoming and outgoing mail server but first you need to check the appropriate box before assigning any value
- Incoming server should be set a port value as “465” and “995” port number should be set to outgoing mail server
- That’s it. You are done and finally have set up Gmail in Microsoft Outlook 2007.
Blocking access to undesirable Web sites through the use of Internet protocol filters has been a common government tactic since commercial Internet access first became available here in 1995. China and Saudi Arabia are believed to extend greater censorship over the net than any other country in the world under the pretext of information control.
Most of the blacklisted sites in Saudi Arabia are either sexually explicit or about religion, women, health, drugs and pop culture. They even block access to websites about bathing suits. So if you want to buy something to swim in, they seem to treat that as if it were pornographic in Saudi Arabia.
In China, webites containing sexually explicit content were among those blocked, but they also included sites on sensitive topics such as Tibet, Taiwan, and dissident activity. China also blocks access to Google News, Typepad and Blogger hosted blogs.
But what if an innocent website is accidentally blocked by your ISP or your government. There are always legitimate reasons to visit these blocked websites. We have listed a few methods to help you access blocked websites in school, college, office or at home.
Approach 1: There are websites Anonymizer who fetch the blocked site/ page from their servers and display it to you. As far as the service provider is concerned you are viewing a page from Anonymizer and not the blocked site.
Approach 2: To access the blocked Web site. type the IP number instead of the URL in the address bar. But if the ISP software maps the IP address to the web server (reverse DNS lookup), the website will remain blocked.
Approach 3: Use a URL redirection service like tinyurl.com or snipurl.com. These domain forward services sometimes work as the address in the the url box remain the redirect url and do not change to the banned site.
Approach 4: Use Google Mobile Search. Google display the normal HTML pages as if you are viewing them on a mobile phone. During the translation, Google removes the javascript content and CSS scripts and breaks a longer page into several smaller pages. [link] View this website in Google Mobile
Approach 5: Enter the URL in Google or Yahoo search and then visit the cached copy of the page. To retrieve the page more quickly from Google's cache, click "Cached Text Only" while the browser is loading the page from cache.
Approach 6: A recent Oreilly story on accessing blocked websites suggested an approach to access restricted web sites using Google language tools service as a proxy server. Basically, you have Google translate your page from English to English (or whatever language you like). Assuming that Google isn’t blacklisted in your country or school, you should be able to access any site with this method. Visit this site via Google Proxy
Approach 7: Anonymous Surfing Surf the internet via a proxy server. A proxy server (or proxies) is a normal computer that hides the identity of computers on its network from the Internet. Which means that only the address of the proxy server is visible to the world and not of those computers that are using it to browse the Internet. Just visit the proxy server website with your Web browser and enter a URL (website address) in the form provided.
The attack is actually quite simple. First job is to be able to sniff data packets and like open Wi-Fi network or any other open network. Download Ferret to copy all the cookies flying through the air. Finally, those cookies are cloned into browser – in easy point-and-click fashion - with a home-grown tool called Hamster.This story has been elaborated by Graham here
The attack can hijack sessions in almost any cookie-based web application and Graham has tested it successfully against popular webmail programs like Google’s Gmail, Microsoft’s Hotmail and Yahoo Mail. He stressed that since the program just uses cookies, he only needs an IP address and usernames and passwords aren’t required.
He has also included a slideshow here:Gmail hacking at Blackhat
If you want to prevent your accounts from being hacked then force https throughout a gmail session.Change your http://mail.google.com bookmark to https://mail.google.com. Or type in the full URL in your browser starting with https://, or else your browser will assume http:To ensure that your entire gmail session uses https, grab the GmailSecure greasemonkey script:
http://userscripts.org/scripts/show/1404
Today an interesting advisory about some vulnerabilities affecting Orkut - the famous social networking website, owned by Google.
There are several cases like -Sometimes the application may lock out the user to the main page when an operation fails, asking the user to login again, but failing to logout the user while doing it. This could confuse the users into thinking that they logged out.
And Now a hacker can use this stage for hacking the users account.At this stage the "orkut_state" cookie can still be used to login successfully, even if the user logged out. This is probably due to a failure to mark the session as expired on the server side.
How to?-A Technical Description(Never use this info to hack any others account)
On successful Orkut login, the following cookies are set:-
1. Domain: .www.orkut.com Cookie: orkut_state
2. Domain: .google.com Cookie: SID
3. Domain: www.google.com Cookie: LSID
Secure Yourself from Hackers & Hijackers |
| |
| Hackers and Browser Hijacking is one area of the Net that affects everyone at some stage. In addition to having third party utilities such as SpyBot, Anti Virus scanners and firewalls installed there are some changes that can be made to Windows 2000/XP. Below are some details to make your system safer from hackers and hijackers. Some of these tips require editing of the Registry so it is wise to either backup the registry and/or create a Restore Point. |
Windows 2000/XP paging file (Sometimes called the Swap File) can contain sensitive information such as plaintext passwords. Someone capable of accessing your system could scan that file and find its information. You can force windows to clear out this file.
In the registry navigate to HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerMemory Management and add or edit the DWORD ClearPageFileAtShutdown. Set it to 1.
Note that when you do this, the system will take much longer to shut down: a system with a really big Page File (! Gig or more) may take a minute or two longer.
2. Disable the POSIX and OS/2 Subsystem.
Windows 2000 and XP come with little-documented subsystems it at allow compatibility with UNIX and OS/2 systems These rues systems are enabled by default but so rarely used that they are best off bring disabled completely to prevent possible service hijackings.
To disable these subsystems, open the registry and navigate to HKEY LOCAL MACHINESYSTEMCurrentControlSetControlSession ManagerSubSystems. Delete the subkeys Os2 and Posix. then reboot.
| 3. Never leave default passwords blank. On installation, Windows 2000 sets up an Administrator account with total system access and prompts for a password. Guess what: by default, it allows that password to be blank. If a user doesn't want to type a password, he can simply click Next and the system will be an open door for anyone who wants to log on. Always opt for a password of some kind when setting up the default account on a machine. 4. Disable the Guest account Windows XP comes with a Guest account that's used for limited access, but it's still possible to do some damage with it. Disable it completely if you are not using it. Under Control Panel, select User Accounts, click on Guest Account and then select Turn Off the Guest Account. |
Windows usually installs itself in the WINDOWS directory. Windows NT 4 0 and 2000 Will opt for WINNT. Many worms and other rogue programs assume this to be the case and attempt to exploit those folders files. To defeat this install Windows to another directory when you're setting it up - you can specify the name of the directory during setup. WINDIR is okay; so some people use WNDWS - A few (not that many) programs may not install properly if you install Windows to another folder but t hey are very few and they are far between
6. Fake out hackers with a dummy Administrator account
Since the default account in Windows 2000 is always named Administrator, an enterprising hacker can try to break into your system by attempting to guess the password on that account. It you never bothered to put a password on that account, say your prayers.
Rather than be a sucker to a hacker, put a password on the Administrator account it you haven't done so already. Then change the name of the Administrator account. You'll still be able to use the account under its new name, since Windows identifies user accounts by a back-end ID number rather than the name. Finally, create a new account named Administrator and disable it. This should frustrate any would -be break-ins.
You can add new accounts and change the names of existing accounts in Windows 2000 through the Local Users and Groups snap in. Right-click on My Computer, select Manager, open the Local Users and Groups subtree, look in the Users folder and right-click on any name to rename it. To add a new user, right-click on the containing folder and select New User. Finally, to disable an account, double-click it, check the Account is disabled box and click OK.
Don't ever delete the original Administrator account. Some programs refuse to install without it and you might have to log in under that account at some point to setup such software. The original Administrator account is configured with a security ID that must continue to be present in the system.
7. Set the Hosts file to read-only to prevent name hijacking.
Unfortunately hijackers and hackers also love to put their own information into it - redirecting people from their favorite sites to places they don't want to go. One of the most common entries in HOSTS is local host which is set 1770.0.1. This refers to the local machine and if this entry is damaged the computer can behave very unpredictably.
To prevent HOSTS from being hijacked, set it to read-only. Go to the folder %Systemroot%system32driversetc, right-click on HOSTS, select Properties check the Read-Only box and click OK. If you want to add your own entries to HOSTS, you can unprotect it before doing so, but always remember to set it to read-only after you're done.
| 8. Turn off unneeded Services Windows 2000 and XP both come with many background services that don't need to he running most of the time: Alerter, Messenger, Server (If you're running a standalone machine with no file or printer shares), NetMeeting Remote Desktop Sharing, Remote Desktop Help Session Manager (the last two if you're not using Remote Desktop or NetMeeting), Remote Registry, Routing and Remote Access (if you're not using Remote Access), SSDP Discovery Service, Telnet, and Universal Plug and Play Device Host. A good resource and instruction on which of these services can be disabled go to /http://www.blkviper.com/WinXP/ |
This is another anti hijacker tip. IE can be set so that any changes to its settings must be performed through the Internet icon in the Control Panel, rather than through IE's own interface. Some particularly unscrupulous programs or sites try to tamper with setting by accessing the Tools, Options menu in IE. You can disable this and still make changes to IE's settings through the Control Panel.
Open the Registry and browse to HKEY_CURRENT_USER SoftwarePoliciesMicrosoftInternet ExplorerRestrictions. Create or edit a new DWORD value named NoBrowserUptions and set it to 1 (this is a per-user setting). Some third-party programs such as Spybot Search And Destroy allow you to toggle this setting.
You can also keep IE from having other programs rename its default startup page, another particularly annoying form of hijacking. Browse to HKEY.CURRENT USERSoftwarePolicies MicrosoftInternet ExploreControl Panel and add or edit a DWORD, Homepage and set it to 1.
10. Disable simple File Shares.
In Windows XP Professional, the Simple File Sharing mode is easily exploited, since it抯 a little too easy to share out a file across your LAN (or the NET at large). To turn it off, go m My Computer, click Tools, Folder Option and the View tab, and uncheck Use Simple file sharing (Recommended). Click OK. When you do this you can access the Security tab in the Properties window for all folders; set permissions for folders; and take ownership of objects (but not in XP Home)

Google trick -2 Top 10 Cool Google Search Tricks
- Google trick to search different file formats (keyword filetype:doc)
- Google trick to search educational resources (keyword site:.edu) example (computer site:.edu)
- Finding the time of any location (time romania)
- Finding the weather of any location (boston weather)
- Tracking commentary of live events (Olympic games Beijing 2008)
- Using Google as a calculator (9 * 10)(143+234)(119-8)
- Converting currencies (1 USD in INR)(10 US Dollars in Indian Rupee)
- Find how many teaspoons are in a quarter cup (quarter cup in teaspoons)
- how many seconds there are in a year (seconds in a year)
- Tracking stocks (stocks:MSFT)
- Finding faces (add imgtype=face to the URL)
#1: Get Local Weather
#2: Check Flight Status
#3: Convert Distances
#4: Find a Phone Number
Find a Person:
Find a Business/store:
#2 site:rapidshare.de inurl:users "*"
#3 site:rapidshare.com inurl:files "*"
#4 site:rapidshare.de inurl:files "*"
#5 site:rapidshare.com inurl:users (pass|password)
#6 site:rapidshare.de inurl:users (pass|password)
Suppose u need some info on ebooks. Then u can try following keyword to see all rapidshare folders having any hacking related thing in it
site:rapidshare.com inurl:users "ebooks"
| As more and more people get quick connections to the internet, such as cable or ADSL, it becomes apparent to the user of a simple dial-up modem that the World Wide Web can quickly turn into the World Wide Wait. Here a trick that can help speed up your current modem without shelling out the big bucks. There is a setting located in your windows registry called the Maximum Transfer Unit (MTU). This determines the size of the packets of data sent between your and your server. In Windows 95, this setting is has a value of 1,500 bytes when the actual size of internet packets is 1,000 bytes. This can sometimes slow things down. To remedy the situation, simply follow these steps: In the registry editor (Start > Run > regedit.exe), navigate to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Class\NetTrans. In the NetTrans folder you should find another folder named "000x" in which x represents a fourth digit. Right-click on the "000x" folder and select New and StringValue. Rename the item that appears in the panel on the right side to MaxMTU, then double-click it to bring up the Edit String box and give it a velue of 1002. Remember to keep playing with the MaxMTU value until you feel that your internet connection has greatly sped up. Some people report huge speed gains using this tricks, while others hardly notice a difference. In any case, it's definetly worth a try. |
| Microsoft reserves 20% of your available bandwidth for their own purposes like Windows Updates and interrogating your PC etc You can get it back: Click Start then Run and type "gpedit.msc" without quotes. This opens the group policy editor. Then go to: --> Local Computer Policy --> Computer Configuration --> Administrative Templates --> Network --> QOS Packet Scheduler --> Limit Reservable Bandwidth. Double click on Limit Reservable bandwidth. It will say it is not configured, but the truth is under the 'Explain' tab i.e." By default, the Packet Scheduler limits the system to 20 percent of the bandwidth of a connection, but you can use this setting to override the default." So the trick is to ENABLE reservable bandwidth, then set it to ZERO. This will allow the system to reserve nothing, rather than the default 20%.It works on Win 2000 as well. |
| Multiple login in yahoo Without Using any Software You can login with multiple id's on the same yahoo messenger without any download or patch . Follow these steps : 1. Go to Start ----> Run . Type regedit, then enter . 2. Navigate to HKEY_CURRENT_USER --------> Software ---> yahoo --->pager---->Test 3. On the right page , right-click and choose new Dword value . 4. Rename it as Plural. 5. Double click and assign a decimal value of 1. Its done!! Now close registry and restart yahoo messenger and try Multiple Login |
| Sometimes some of your friends who appear offline in yahoo messenger may not be actually offline, they may in the 'Invisible' mode. This maybe if they are trying to ignore you or are too busy to talk to anyone. There is this small trick that you can use to find out what the truth is. Firstly open your yahoo messenger main window and double click on the name of the person whom you want to check. The chat window will open obviously. Click IMVironment button, select See all IMVironments, select Yahoo! Tools or Interactive Fun, and click on Doodle. After loading the Doodle imvironment there can be two possibilities 1.If the user is offline Doodle are will show this "waiting for your friend to load Doodle" continuously .See in the picture below: 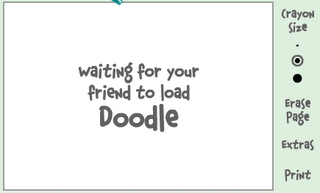 2. If the user is online (but in invisible mode), after few seconds (it can take up to one minute, depending on your connection speed), you should get a blank page like in the picture below. So you know that the user is online.  |
| Just follow the simple steps Below: 1) Right click on the Google Talk shortcut. 2) click on Properties. 3) Go to Shortcut tab on Google Talk Properties window. 4) On the Target textbox, add in the /nomutex to the end of the line so that it looks like below (or you can simply copy and paste the below syntax and replace the original). “c:\program files\google\google talk\googletalk.exe” /nomutex 5) Click on OK. I didn't have to do anything after this and clicking on the shortcut multiple times just gave me different Google talk window. Alternative To create a new shortcut for Google Talk: 1) Right-click on the desktop or anywhere you want to place the GTalk shortcut. 2) Select New on the right click context menu. 3) Then select Shortcut. 4) Copy and paste the following line to the text box when prompted to type the location of the item: “c:\program files\google\google talk\googletalk.exe” /nomutex 5) Click on Next. 6) Give the shortcut a proper name such as Google Talk or Google Talk Multiple or Google Talk Polygamy. 7) Click OK until you are done. |
| This Firefox tricks will improve the speed & load time of firefox. And you will be able to surf faster. Type about:config in the address bar, Then look for the following entries, and make the corresponding changes. network.http.max-connections-per-server =32 network.http.max-persistent-connections-per-proxy =16 network.http.max-connections = 64 network.http.max-persistent-connections-per-server = 10 network.http.pipelining = true network.http.pipelining.maxrequests = 200 network.http.request.max-start-delay = 0 network.http.proxy.pipelining = true network.http.proxy.version = 1.0 Lastly right-click anywhere and select New- Integer. Name it nglayout.initialpaint.delay and set its value to 0. This value is the amount of time the browser waits before it acts on information it receives. Enjoy!! |
| Yahoo messenger is one of the mostly used chatting application accross the globe. So, Yahoo has many built in hidden emotions like laughing yahoo emotions, sad yahoo emotions, oncall, busy yahoo emotions and many more.. Below images contains all the yahoo emotions. 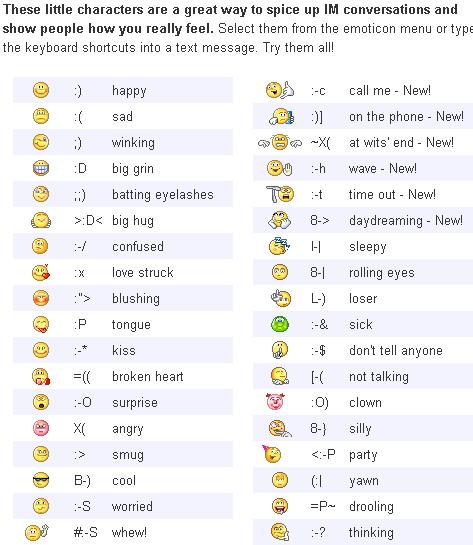 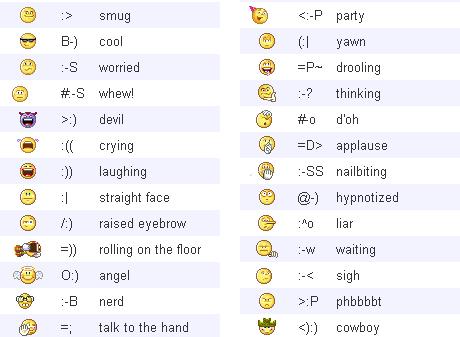 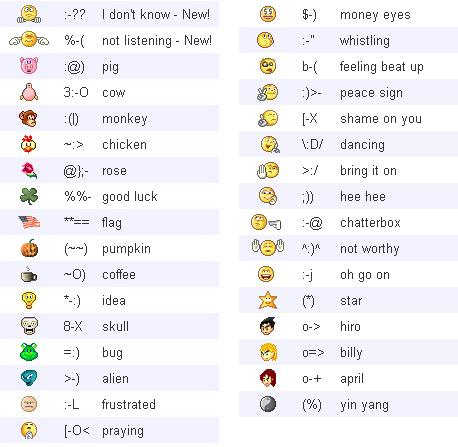 |
Top Tips to increase bittorent download Speed
| The latest file sharing protocol bittorrent has modified everything when it comes to file sharing. It is a nice platform for downloading large files. Sharing of files include movies, iso images and MP3 songs. Bittorent is mainly famous for illegal file sharing . The Bittorrent system can be slow at times due to heavy traffic. so let us tweak bittorrent sharing program a little bit. There are a lot of different bittorrent clients that you can download. I think the best are BitCommet and uTorrent. Here is a few tips to speed up uTorrent Client. Similar can be implemented on any other torrent clients ,which you are using. Step 1: Increase TCP connections You need to increase the number of TCP connections that are allowed at max.Windows XP Service Pack 2 came with the number of allowed open connections to 10. This is to stop any piece of spyware(in our case bittorent client even) from totally taking over your internet connection. TCP connection allowed should be 50 for optimal performance. The best way to increase the maximum number of connections is to apply patch that is available at www.lvllord.de. A nice way to fix this is to download this patch . The little tweak to the torrent client works great in certain times. If you’re using uTorrent go to Options menu then Preferences. In the Preferences go the Advanced Options. In the advanced options change the net.max_halfopen connections to 80. In the same section change the max half open tcp connections to 80. Once your done click on OK and you are all set. This tweak will let the maximum TCP connection available for the bittorrent client. Now start downloading you’ll realize a little difference in the download speed. Port forwarding technique is more effective than this. A third point of interest is that some “windows updates” revert your tweaked tcp connections back to 10. So it’s wise to check this every now and then. You can check this by going to (in windows xp) Start > Control Panel > Administrative Tools > Event Viewer > System… Look for event 4226 (sort by event). If there are a lot of daily occurrences it’s likely that the max amount of half-open tcp connections was set back to 10. Or you’re infected with some nasty spy ware… Step 2:Torrent Client Configuration In order to apply these tips you must know your maximum up- and download speed. You can test your bandwidth over here (stop all download activity while testing). Settings 1-4 can be found in the options, settings or preference tab of most torrent clients. 1. Maximum upload speed Probably the most important setting there is. Your connection is (sort of) like a pipeline, if you use you maximum upload speed there’s not enough space left for the files you are downloading. So you have to cap your upload speed. Use the following formula to determine your optimal upload speed… 80% of your maximum upload speed so if your maximum upload speed is 40 kB/s, the optimal upload rate is 32kB/s But keep seeding! |
Total Pageviews
Clock
Popular Posts
-
I love Google, Bing and Yahoo just as much as the next Internet user, but sometimes you really want to dig down into a particular subject....
-
Battleship (2012) - 1Cd - SCamRip - {Telugu} Dubbed Battleship (2012) - 1Cd - SCamRip - {Telugu} Dubbed - X264 - AAC.mkv@Aditya (Size: ...
-
Magadheerudu (2012) Telugu Dubbed 1CD R5 DVDRip x264 MP3.mkv 698.47 MB Magadheerudu Telugu Dubbed Movie Download: HERE Descri...
-
Men In Black 3 Telugu Dubbed (Size: 587.31 MB ) seeders: 92 leechers: 189 Men In Black 3 Telugu Dubbed Movie Download : HER...
-
Neekosame Na Anweshana (Male & Female) 320kbps Click here to download Nee Kosam Naa Anweshana[Female] mp3 (320kbps-0.54MB) Click here...
-
Osama bin Mohammed bin Awad bin Laden is still alive in nuristan, afghanisthan. President Barack Obama has decided not to release any photos...
-
.:: Song Name : Kevvu Keka ::. Cast : Pawan Kalyan, Shruti Hassan Music : Devi Sri Prasad Singers : Mamta Sharma, Kushi Murali Lyri...
-
Boy was following a Girl. GIRL-why r u folowin me? BOY -you r very pretty n I think I'm in Love wid u! GIRL-but u havnt met my ...
-
NAGAVALLI Telugu Full Movie 2010 HQ Cam DVD Rip Movie: Nagavalli (2010) Cast: Venkatesh, Anushka Shetty, Richa Gnagopadyay, Kamalini Mukarj...
-
This is a list of Governors of Andhra Pradesh since in 1953. The official residence is of the Governor is Raj Bhavan, situated in Hydera...
My site Traffic






